
Effective Ways to Get Rid of Spam Phone Calls
Spam phone calls have become one of the most frustrating nuisances for many people today. From scam calls to telemarketers, these unwanted interruptions can invade

Spam phone calls have become one of the most frustrating nuisances for many people today. From scam calls to telemarketers, these unwanted interruptions can invade

Ensuring the safety and security of your home and loved ones is more important than ever. One of the most effective ways to increase your

Oppenheimer (2023) – A Christopher Nolan biopic about J. Robert Oppenheimer and the development of the atomic bomb. Barbie (2023) – A creative and comedic take on

The 4th of July, also known as Independence Day, is one of the most cherished national holidays in the United States. It symbolizes freedom, patriotism,
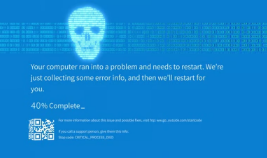
The Blue Screen of Death (BSOD), also known as a stop error, is one of the most dreaded experiences for Windows users. When your computer
Using two-factor authentication (2FA) enhances security, but certain issues can arise if not managed properly. These include: Login Difficulties: If you forget or lose access

Security is a critical concern for small business offices. Protecting sensitive data, customer information, and internal operations can prevent costly breaches and maintain trust. Here

What Is ‘Tell Me’? ‘Tell Me’ is a smart, user-friendly command box available in Microsoft Office 2016 and later versions. Located at the top of

As temperatures soar during summer, many car owners are faced with the dilemma of leaving devices such as smartphones, tablets, or even portable chargers inside

A great graduation gift for a tech-savvy person combines utility, innovation, and personalization. Here are some excellent ideas: Smartphone Accessories Wireless earbuds or headphones (e.g.,

What Are Macros? Macros are sequences of recorded commands or scripts that automate tasks in Excel. Once recorded, you can run a macro to perform

Father’s Day is a special occasion dedicated to honoring and appreciating fathers and father figures around the world. Usually celebrated on the third Sunday of

Flag Day is a special occasion celebrated in various countries around the world, most notably in the United States on June 14th. This day commemorates

Terms like megabytes (MB) and gigabytes (GB) are everywhere—when talking about storage, downloads, or data transfer. But what do these units really mean? What is

As technology rapidly advances, many of us find ourselves with outdated or unused computer equipment cluttering our homes or offices. Instead of letting these devices

Hashtags are words or phrases preceded by the “#” symbol, like #Travel or #Fitness. They are used primarily on social media platforms to categorize content,

Computer viruses are malicious software programs designed to harm, disrupt, or gain unauthorized access to your computer system. There are various types of viruses, each

A streaming service is a digital platform that allows users to watch, listen to, or access content instantly over the internet without needing to download

Seniors are often targeted because they may be less familiar with digital technology or more trusting of strangers. Fortunately, with awareness and proactive measures, you

Staying focused can be a challenge. Fortunately, technology offers tools to help you manage your time better and stay on track. Here are the top

Staying connected with loved ones has never been easier thanks to the wide variety of messaging and video call apps available today. Whether you want

Social media has become a powerful way to connect with friends, family, and the world. It offers countless benefits—from staying in touch to sharing memories—but

Here’s a simple guide on how to back up your important data effectively: 1. Use Cloud Storage Services Cloud storage allows you to store your

Screens are a constant presence in our lives—from smartphones and tablets to computers and TVs. While technology offers numerous benefits, excessive screen time can negatively

A strong, stable Wi-Fi connection is essential for seamless browsing, streaming, and working from home. However, many people overlook one of the most critical factors

Memorial Day is a special day in the United States that holds deep significance. Observed annually on the last Monday of May, it’s a time

Email scams are more prevalent than ever, and scammers often use simple tricks to deceive unsuspecting victims. While some scams can be sophisticated, many are

In our busy lives, juggling work, family, and personal interests can sometimes feel overwhelming. Fortunately, ChatGPT is here to help simplify your routine, answer your

As our population ages, finding ways to support the independence of older adults has become increasingly important. Bluetooth technology, often associated with wireless headphones or

One of the more insidious methods targeting unsuspecting individuals is known as smishing. But what exactly is smishing, and how can you protect yourself from

Here are seven cool tricks for taking great photos with your iPhone: Use Gridlines: Enable the gridlines on your iPhone by going to Settings >

If a debt collector is asking you to buy gift cards as a method of payment, it’s important to approach this situation with caution. Here

Tech jargon can often be confusing, especially for those not deeply immersed in the technology world. Here’s a breakdown of some common tech terms and

Proper maintenance of your cell phone can enhance its performance, extend its lifespan, and ensure security. Here are some essential maintenance tasks that everyone should
The challenges of cyber threats, data breaches, and identity theft are omnipresent in our digitally connected world. Strong, well-managed passwords serve as a crucial barrier

Machine learning (ML), a subset of artificial intelligence, is emerging as a transformative tool that helps companies understand their customers better, personalize interactions, and anticipate

What is Blockchain Technology? At its core, blockchain is a distributed ledger technology (DLT) that securely records transactions across many computers. This decentralized approach ensures

Mother’s Day is a special occasion dedicated to honoring the incredible women who have nurtured, guided, and shaped our lives. As we celebrate this day,

Individuals across various industries are discovering the benefits and challenges of working from home. Remote work offers flexibility, productivity, and the ability to create a

Computers have become an integral part of our lives. However, like any complex technology, they can sometimes encounter issues that hinder their performance. Here are

Every device that connects to the internet is assigned a unique identifier known as an Internet Protocol (IP) address. But what exactly is an IP

The term “computer bug” is a commonly used phrase to describe faults or glitches within a computer system. But did you know that the origin

Rain can negatively affect internet connections, particularly for certain types of technology. Here’s how it can impact them: Satellite Internet: Heavy rain can interfere with

In the vast landscape of the internet, domain names serve as crucial identifiers for websites. Among the most recognized domain extensions are .com and .net,

Every year, fans around the globe eagerly mark May 4th as Star Wars Day, a playful nod to one of the franchise’s most iconic lines:

Here are some popular keyboard shortcuts that can enhance your productivity and efficiency while using a computer: For Windows: Ctrl + C: Copy selected item

Businesses rely heavily on their IT infrastructure to operate efficiently and remain competitive. Just like regular maintenance is crucial for your vehicle or office space,

Preventing your cell phone from being compromised is essential for maintaining your privacy and security. Here are several effective strategies to help safeguard your device:

Texting has become a primary means of communication for many teens and young adults, and understanding how to engage effectively can enhance your interactions. Here

Understanding how cookies and cache work is essential for maintaining your online privacy and optimizing your browsing experience. But how often should you be deleting

Choosing the right laptop can be a daunting task with the plethora of options available on the market. Whether you need a device for work,

Many people are considering whether they need a Virtual Private Network (VPN) for their home internet use. A VPN can offer various benefits, but it’s

Spam emails can clutter your inbox, decrease productivity, and pose security risks. While it may be impossible to eliminate spam completely, there are several effective

Investing in a robust security system is a crucial step toward protecting your property and ensuring peace of mind. With a variety of security options

Voice over Internet Protocol (VoIP) has fundamentally changed the way we communicate, offering cost-effective and flexible alternatives to traditional telephone services. As we look ahead,

Detecting and preventing phishing attacks is crucial for maintaining cybersecurity. Here are some strategies in both areas: Detection Methods: Email Filtering: Use advanced email filters

A blue screen indicating BitLocker recovery typically appears when your computer detects a potential security risk related to your system’s drive. BitLocker is a disk

Surveys are a powerful tool for gathering feedback, conducting research, and understanding your audience’s needs. Microsoft Forms provides a user-friendly platform for creating surveys, quizzes,

Easter is one of the most celebrated holidays around the world, rich with traditions, symbolism, and cultural significance. Falling on a Sunday in March or

Keyboard shortcuts are one of the best ways to boost your efficiency when using Microsoft Office applications like Word, Excel, PowerPoint, and Outlook. Here’s a
Data visualization is an essential skill for turning complex data sets into easily digestible visual representations. Microsoft Excel, a powerful tool widely used for data
Unlocking your cell phone without remembering the code can be frustrating, but there are several methods you can try, depending on your device and the

In the digital age, where cyber threats are on the rise and data breaches can have catastrophic consequences, effective IT security is a top priority

To determine whether your computer is using a Solid State Drive (SSD) or a Hard Disk Drive (HDD), you can use several methods depending on

Yes, Internet Service Providers (ISPs) can throttle, or intentionally slow down, the internet speeds of certain users or types of traffic on their networks. Here’s

The journey of computer technology has been remarkable, transforming from basic calculating machines to advanced systems that power our daily lives. Understanding this evolution helps

When it comes to upgrading your computer or purchasing a new one, one of the most crucial components to consider is the storage drive. The

When discussing computer hardware, four main points are typically highlighted: 1. Central Processing Unit (CPU) The CPU is often referred to as the “brain” of the

Scams are becoming more sophisticated, making it essential to stay vigilant. Here are some key tips to help you identify potential scams and protect yourself.
Productivity is essential for success in both personal and professional realms, yet many individuals and teams fall prey to common mistakes that hinder their effectiveness.

Recovering a lost file can vary depending on how the file was lost and the operating system you are using. Here are some common methods

If your iPad is stuck on a black screen, there are several steps you can try to resolve the issue. Here are some troubleshooting methods:

Thermal paste, also known as thermal compound or thermal interface material (TIM), is a substance applied between the CPU (or GPU) and its heatsink to

A computer in S mode refers to a specific configuration of Windows 10 and Windows 11 that is designed for security and performance. In S

Choosing a strong password is crucial for protecting your online accounts. Here are some good password attributes to consider: 1. Length At Least 12 Characters:

Home security cameras are an essential component of modern home security systems, providing peace of mind and protection against potential intruders. Here’s a beginner’s guide

Learning basic computer skills is essential for navigating the digital world. Here are some key skills that beginners should focus on: 1. Using the Operating System

April 1st is a special day dedicated to humor and playful mischief—April Fools’ Day! For centuries, this day has inspired people around the world to

Cybersecurity and data security are critical concerns for individuals and organizations alike, especially with the increasing sophistication of cyber threats. Here are some of the

Troubleshooting issues in Microsoft Office can help you resolve common problems and enhance your productivity. Here are some frequent issues and their solutions: 1. Office Applications

Editing photos on your iPhone can elevate your images and help them look polished and professional. Here’s a step-by-step guide to editing your iPhone photos

OpenAI GPT-4o mini Disposing of old computers and electronics responsibly is crucial for environmental protection and personal data security. Here are the steps to follow:

Cleaning your computer from dust is essential for maintaining its performance and preventing overheating. Here’s a step-by-step guide to help you clean your computer safely

“Apple Intelligence” typically refers to the various artificial intelligence (AI) and machine learning (ML) technologies developed and utilized by Apple Inc. in its products and

Quantum computing is a type of computation that uses the principles of quantum mechanics to process information. Unlike classical computers, which use bits as the

The future of technology over the next decades is likely to be influenced by several trends and developments: In 10 Years (2035) AI and Automation:

If text messages are going to your iPad but not your iPhone, there are a few possible reasons: iMessage Settings: Check if iMessage is enabled

Keeping your computer in good working condition is essential to ensure longevity and peak performance. Preventative maintenance can help you avoid costly repairs and data
Workflow automation software is a type of technology designed to streamline and automate business processes by managing repetitive tasks and workflows. It helps organizations increase

Microsoft Teams has become an essential tool for collaboration and communication in both remote and in-office settings. To make the most out of this platform,

Leveraging technology is essential for increasing productivity, collaboration, and security in the workplace. Here are ten IT practices and tools that every office should consider

If you’re a Skype user, especially in light of recent changes and Microsoft’s shift towards Microsoft Teams as a primary communication tool, here are some

St. Patrick’s Day, celebrated every year on March 17th, is a global celebration of Irish culture and heritage, honoring Saint Patrick, the patron saint of

To determine if your computer can be upgraded to Windows 11, you should check several hardware and software requirements outlined by Microsoft. Here’s how to
Facial recognition technology (FRT) has rapidly become a transformative tool in various industries, enhancing both identification and security processes. Leveraging artificial intelligence and machine learning,

A signal booster, also known as a range extender or repeater, is a device designed to enhance or extend the coverage area of a wireless

Cryptocurrencies have gained significant attention and popularity over recent years. Understanding the basics of cryptocurrencies is essential, whether you’re considering investing or simply wanting to

In the rapidly evolving digital landscape, possessing a versatile skill set is essential for success in both personal and professional realms. As technology continues to

Optimizing your smartphone’s battery life is essential for ensuring that your device lasts throughout the day without needing frequent recharges. Here are some effective strategies

As the world increasingly embraces digital transformation, the landscape of payment systems is evolving rapidly. Digital payments are becoming a fundamental part of everyday transactions,

As we look ahead to 2025, several tech companies are poised to significantly influence the industry and shape the future of innovation. Here are the

Wearable technology has significantly evolved from its early days, expanding far beyond simple fitness trackers to encompass a wide range of applications and innovative devices.

As organizations continue to adapt to this new working landscape, remote collaboration tools have become essential for maintaining productivity and connectivity. Here’s an overview of

Microsoft has made Windows 11 available as a free upgrade for eligible Windows 10 users. However, you will not be “forced” to upgrade if your

Protecting your privacy in the age of Big Data requires proactive measures and an understanding of how your personal information is collected, used, and shared.

Troubleshooting Speaker Issues Check Volume Settings: Ensure that the volume is turned up. You can adjust the volume using the physical volume buttons on the

Mass emailing users with different variables, commonly referred to as “personalized mass emailing” or “mail merge,” can be effectively accomplished using tools like Microsoft Word

BitLocker is a disk encryption feature available in certain editions of Microsoft Windows, such as Windows 10 Pro, Enterprise, and Education, as well as older

To determine if your router needs an update or patch, you can follow these steps: Check the Current Firmware Version: Log in to your router’s
February 29th, also known as Leap Day, occurs only in leap years, which add an extra day to the month of February to keep our

Fat Thursday, also known as “Tłusty Czwartek” in Poland, is a festive occasion that falls on the last Thursday before Ash Wednesday, marking the beginning

Automating repetitive tasks in Excel can save you significant time and reduce errors. Here are several methods to accomplish this: Use Macros: Recording a Macro:

Phishing attempts can take various forms, but there are common signs to watch out for that can help you identify them. Here are key indicators

Here are some common types of tech support scams that individuals and businesses should be aware of: Fake Technical Support Calls: Scammers often call claiming

If your laptop touchpad is not working, it can be due to several reasons. Here are some common causes and troubleshooting steps: Disabled Touchpad: Sometimes,

Increasing your cybersecurity focus involves adopting a multi-faceted approach to protect your personal and organizational data. Here are several strategies to enhance your cybersecurity awareness

If someone used your email address to send phishing emails, here are steps you can take to prevent this from happening: Change Your Password: Immediately

Troubleshooting hardware issues involves systematically identifying and resolving problems with your computer’s physical components. Here’s a step-by-step guide to help you troubleshoot hardware problems: 1. Perform

Here are some fun and interesting facts about Valentine’s Day: 1. Origins in Ancient Rome Valentine’s Day has its roots in the Roman festival of Lupercalia,

Keeping your software up to date is essential for security, performance, and functionality. Here are some effective strategies to ensure your software stays current: 1. Enable

Detecting whether your system has been compromised involves looking for unusual signs and behaviors. Here are several indicators that may suggest your system has been

Recovering lost or deleted files can often be achieved through several methods, depending on the circumstances of the data loss. Here are some steps you

A slow internet connection can be frustrating and may be caused by a variety of factors. Here are some common reasons why your internet connection

If your computer is running slow or freezing, there are several steps you can take to diagnose and resolve the issue. Here’s a guide to

Here are some highly regarded cloud-based antivirus software options that provide effective protection and a range of features: 1. Webroot SecureAnywhere Overview: A lightweight cloud-based solution

If you receive a phishing email, it’s important to handle it carefully to protect your personal information and computer security. Here’s what you should do:

Effective password management is crucial for maintaining the security of your online accounts and personal information. Here are some best practices to follow: 1. Use Strong

Browsing the internet safely is essential to protect your personal information and maintain your privacy. Here are some effective strategies to help you stay safe

Improving your computer’s performance can enhance your overall user experience. Here are several strategies to boost your computer’s speed and efficiency: 1. Upgrade Hardware Increase RAM:

Backing up your data is essential to prevent loss from hardware failures, accidental deletions, or other unforeseen events. Here are several methods you can use

Cloud storage and local storage are two different methods for storing data, each with its own characteristics and advantages. Cloud Storage: Definition: Data is stored

Upgrading to a new operating system (OS) can offer several benefits, including: Enhanced Security: Newer operating systems often include improved security features and patches for

There are several reasons why you might not have received text messages sent to your iPhone. Network Issues: There may have been a temporary network

If your computer made a sound and then stopped working, it may indicate a hardware issue or a system malfunction. Here are some steps you

Effective scheduling and collaboration are essential for maintaining productivity and ensuring smooth operations. Microsoft Outlook is more than just an email client; it is a

As technology continues to evolve at a rapid pace, software companies must make tough decisions about when to phase out older products. One significant milestone

Routers rented from ISPs can be perceived as slower for several reasons: Basic Models: ISPs often provide basic or outdated router models that may not

Data privacy has become a hot topic of discussion among individuals, businesses, and governments. With personal information shared and stored online, understanding data privacy is

Many people struggle with the decision to take time off work or school when they feel under the weather. However, understanding when to stay home

While you may not be able to completely turn off ads on Facebook, you can take steps to reduce the number of ads you see

If your tablet is running slowly, there are several steps you can take to improve its performance. Here’s a guide to help you speed up

Shared spreadsheets have become an essential tool for teams, families, and individuals working on projects, budgets, or organizing events. A shared spreadsheet allows multiple users

A YubiKey is a small, portable device used for two-factor authentication (2FA) and secure access to online accounts and services. Developed by Yubico, YubiKeys provide

Web hosting is a service that allows individuals or organizations to make their websites accessible on the internet. It involves storing website files on a

Your Wi-Fi router plays a critical role in this connectivity, serving as the gateway to the online world for all your devices. One common question

Yes, a router can be vulnerable to hacking if proper security measures are not implemented. Here are some common methods through which a hacker might
Using a spreadsheet can greatly assist in the tax filing process by helping you organize and calculate financial information efficiently. Here are several ways a

Having a camera system in place can provide various benefits across different contexts, whether for personal, business, or security purposes. Security and Surveillance: One of

Data is one of the most valuable assets for individuals and businesses alike. From important documents to sensitive customer information, the loss of data can

Here’s a step-by-step guide to help you clean up your iCloud storage: Step 1: Check Your iCloud Storage On iPhone/iPad: Go to Settings. Tap your name

The age at which a computer can be considered “too old” varies depending on several factors, including usage requirements, hardware capabilities, and software compatibility. Here

Data integrity is crucial in any data-driven workspace. One powerful tool in Excel for maintaining accuracy and consistency in your datasets is Data Validation. This

Here are some interesting facts about New Year’s Day: Ancient Origins: The celebration of the new year dates back over 4,000 years. The ancient Babylonians

There are several steps you should consider before activating your new cell phone: Back Up Your Data: Ensure that you back up important data (contacts,

To unblock apps on a Nighthawk router, follow these general steps: Log into the Router: Open a web browser and enter the router’s IP address

Troubleshooting a printer that is showing as offline involves several steps. Here’s a systematic approach: Check Printer Status: Ensure the printer is powered on and

Renting a Router from an ISP Pros: Lower Initial Cost: You typically pay a lower upfront cost, as there are no large investments required. Cons:

Here are three fun Christmas Day facts: Global Celebration: Christmas is celebrated by millions of people around the world, and it is a public holiday

One of the best tips for using Microsoft Outlook effectively is to organize your emails with folders and rules. How to Implement This Tip: Create

Deciding whether to repair a computer or buy a new one depends on several factors. Here are some considerations to help you make that decision:

Are you looking for the perfect gift this holiday season but can’t seem to find something that fits? Look no further! We are excited to

The Winter Solstice, occurs around December 21st in the Northern Hemisphere. This significant date marks the shortest day and longest night of the year, a

If your Facebook account says you’re locked out, here are steps you can take to regain access: Go to the Login Page: Try to log

The integration of security cameras into residential spaces has emerged as a significant trend. With technological advancements making these systems more accessible and effective, security

Augmented reality (AR) glasses are emerging as one of the most exciting innovations set to reshape how we interact with the world around us. Blending

While specific details about tech gadgets set to be released in 2025 may not be fully known yet, here are some expected trends and innovations

Your computer plays a crucial role in your daily activities, whether for work, school, or entertainment. However, like any electronic device, it can encounter issues

IT Business Services encompass a wide range of services that support the technology needs of an organization. These services are designed to help businesses operate

Origin of Christmas Trees: The tradition of decorating Christmas trees dates back to 16th-century Germany. People would bring evergreen trees into their homes and adorn

A zero-day refers to a security vulnerability in the Windows operating system that is unknown to the software vendor (in this case, Microsoft) and has

Internetling occurs when your Internet Service Provider (ISP) intentionally slows down your internet speed, often during peak usage times or if you exceed a certain

If believe your personal data has been compromised, take the following steps: Stay Calm: Panic can lead to decisions that may worsen the situation. Change

The Apple Lisa, launched in 1983, holds a unique place in the history of personal computing. Despite its commercial challenges, the Lisa introduced groundbreaking concepts

Data loss can be a significant threat to both individuals and businesses. Whether it’s due to accidentally deleting files, hardware failures, software corruption, or cyberattacks,

Having an effective website is crucial for attracting and retaining visitors, converting leads, and building your brand. An effective website is not just aesthetically pleasing;

If you find yourself overwhelmed by the number of advertisements you see on Facebook, the good news is that you have control over your ad

Many of us find ourselves frequently pondering whether to leave our computers on or turn them off when they’re not in use. While both options

Saving money in the office is essential for improving efficiency and maintaining a healthy bottom line. Here are five simple strategies that can help organizations

Phishing attacks have become increasingly sophisticated and prevalent. These deceptive tactics are designed to trick individuals into revealing sensitive information, such as passwords or credit

iPads generally cannot be upgraded in the same way that traditional PCs or laptops can. Here are some key points to consider regarding upgrading an

Here are some helpful IT tips for the winter season, focusing on keeping your devices and tech environments running smoothly: 1. Keep Devices Warm Cold temperatures

The question of when to get your child a cell phone is a common dilemma for many parents. With technology becoming ever more intertwined with

Whether you’re a gamer, a professional working from home, or someone who enjoys browsing the internet, performance matters. If your computer is feeling sluggish, you

Here are five great IT-related gift ideas for Christmas: Noise-Canceling Headphones: Ideal for remote workers or those who love gaming. Brands like Sony and Bose

Thanksgiving is celebrated in many different ways across various cultures. Whether it’s a traditional feast, a potluck with friends, or a unique family custom, embracing

As Thanksgiving rolls around each year, one light-hearted tradition grabs the spotlight: the Presidential Turkey Pardon. This unique event, filled with humor and charm, has

When it comes to telecommunications, two primary options are often considered for voice communication: Voice over Internet Protocol (VoIP) and traditional landline services. Each has

Selecting the appropriate network equipment is crucial for ensuring efficient, reliable, and secure connectivity for both home and business environments. The right equipment can improve

Understanding viruses and malware is essential for maintaining the security of your devices and personal information. As cyber threats continue to evolve, awareness of different

Performing a network audit is essential for assessing the health, security, and efficiency of a network. A network audit helps identify weaknesses, ensures compliance with

When setting up a network for home or business use, one of the fundamental decisions you’ll face is whether to use wired or wireless networking.

Networking issues can disrupt connectivity and impact productivity, whether in a home or business environment. Understanding common networking problems and their solutions can help users

Regular Software Updates Keeping your software updated is one of the simplest yet most effective ways to ensure that your devices run smoothly and securely.

More people are working from home than ever before. Creating an efficient and ergonomic home office setup is essential for productivity, comfort, and overall well-being.

A cell phone battery may drain quickly for several reasons. Here are some common factors that could contribute to rapid battery depletion: Background Apps: Many

Here are recommended methods for powering down electronics to ensure their longevity and prevent data loss or hardware damage. General Guidelines Shut Down Properly: For

Augmented Reality (AR) and Virtual Reality (VR) are immersive technologies that alter our perception of the world around us, but they do so in distinct

Google Sheets and Microsoft Excel are both powerful spreadsheet applications, but they have some key differences and advantages. Here’s a comparison of the two: Google

Bitcoin is a decentralized digital currency, often referred to as a cryptocurrency, created in 2009 by an anonymous individual or group known as Satoshi Nakamoto.

Online scams can take various forms, and some of the most common and damaging types that affect users include: Phishing Scams: Description: Phishing scams involve

Managing task bar settings on your Windows PC is straightforward and can greatly enhance your user experience. Here’s how to customize various aspects of the

Honoring Sacrifice Every year on November 11th, the United States comes together to honor the bravery and service of its military veterans. Veterans Day is

Here are some recommended settings and adjustments in the Windows Settings (often equivalent to System Preferences on a Mac) for a better experience: 1. System

The choice between a Mac and a PC depends on your personal needs, preferences, and budget. Here are some key differences and considerations: Operating System:

Windows 11 introduces a range of new features and enhancements designed to improve user experience. Here are five tips and tricks to help you make

When it comes to web browsers and safety, several options are recognized for their strong security features and privacy protections. Here are some of the

To determine whether you are running Windows 10 or Windows 11, follow these steps: Method 1: Using the Settings App Open Settings: Click on the

Today marks an essential day in our democracy—Election Day! Whether you’re a seasoned voter or heading to the polls for the first time, it’s crucial

Not using two-factor authentication (2FA) can expose individuals and organizations to several significant security risks. Here are some of the main risks associated with not

If your Windows PC is running slowly, there are several steps you can take to speed it up. Here’s a helpful checklist to improve your

The world’s first computer, often cited as a significant early example, is the Analytical Engine, designed by Charles Babbage in the 1830s. Although it was

Effective communication is more crucial than ever. As organizations continue to embrace remote work, global teams, and hybrid work models, the need for reliable conferencing

Origins of Halloween: Halloween has its origins in the ancient Celtic festival of Samhain, which marked the end of the harvest season and the beginning

When budgeting for Managed IT Services, the amount a small business should set aside can vary based on several factors, including the size of the

When your computer is not working correctly, the first step is to restart the computer. This simple action can often resolve many common issues by

Every year on October 28, we celebrate National First Responders Day, a time dedicated to honoring and recognizing the brave men and women who serve

While iPhones are generally considered more secure than many other devices, it’s still possible to encounter security risks from clicking links on platforms like Facebook.

The Birth of Text Messaging: A Communication Revolution Texting has become one of the primary forms of communication for billions of people. From coordinating plans

Buffering during streaming can be frustrating. Here are some tips to help reduce or eliminate buffering issues: Check Internet Speed: Ensure your internet connection speed

Review Security Policies: Assess your current security policies and update them as needed to address new threats or changes in business operations. Conduct a Security

Here are some cool tips to enhance your efficiency and productivity when using Excel: Keyboard Shortcuts: Use Ctrl + C to copy, Ctrl + V to paste, and Ctrl +

The computer virus is often considered to be the “Creeper” virus, which was developed in the early 1970s. It was created by Bob Thomas at

As we reach the final week of National Cybersecurity Awareness Month this October, we turn our attention to an exciting yet challenging aspect of our

To help avoid getting a virus on your computer or other devices, consider following these best practices: 1. Use Antivirus Software Install reputable antivirus software and

Disaster Recovery Preparedness Checklist Planning and Documentation Develop a Disaster Recovery Plan Define the scope and objectives. Identify critical business functions and processes. Conduct a

There are several apps available that can help you clean up storage on your cell phone. Here are some popular options: CCleaner: This app helps

Every year on October 16, we celebrate World Food Day, a global event that seeks to raise awareness and inspire action towards ending hunger and

If your desktop computer is getting loud, it could be a sign of several potential issues. Here are some common causes and what you should

As we progress through National Cybersecurity Awareness Month this October, Week 3 focuses on a vital topic: protecting personal information. Understanding how to safeguard personal

There can be several reasons why your phone is getting hot. Here are some common causes: Heavy Usage: Running demanding apps or games can cause

Cleaning up your iCloud storage can help you free up space and ensure that critical files are accessible without running into storage limits. Here are

It’s a good idea to take precautions with your electronics when a bad storm is predicted. Here are some steps you can follow: Unplug Devices:

Every year on October 10, the world observes World Mental Health Day, a day dedicated to raising awareness and promoting mental health education globally. Established

AI (Artificial Intelligence) has a wide range of applications and capabilities across various fields. Here are some things you can do with AI: Natural Language

Blockchain is a decentralized digital ledger technology that records transactions across many computers in a way that the registered transactions cannot be altered retroactively. Each

As we continue our journey through National Cybersecurity Awareness Month this October, the second week focuses on a crucial element of organizational success: creating a

Ensuring the safety of your home and loved ones is more important than ever. One of the most effective ways to enhance your home’s security

Children are growing up surrounded by technology and the internet. While online access provides a world of opportunities for learning, creativity, and connectivity, it also

Efficiency and productivity are paramount, whether you’re working from home, in an office, or anywhere in between. One of the most effective ways to enhance

Employee turnover is an inevitable part of running a business, whether due to voluntary resignation, retirement, or layoffs. While it can be a natural shift,

Businesses depend heavily on technology to streamline operations, enhance communication, and achieve business goals. However, managing IT infrastructure can be complex, time-consuming, and often diverts

As technology continues to advance, our reliance on electronic devices has never been greater. From computers and smartphones to gaming consoles and home appliances, we
As we dive into National Cybersecurity Awareness Month this October, the first week focuses on making our homes a haven for online safety. Understanding the

Businesses of all sizes are under constant pressure to adapt to new technologies and remain competitive. However, many organizations still rely on outdated technology, which

Browser extensions offer many benefits and can significantly enhance your online experience, they also come with certain risks and dangers. Here are some of the

Deepfake is a sophisticated form of artificial intelligence (AI) used to create realistic-looking fake videos, audio recordings, or images. The term “deepfake” combines “deep learning,”

October is designated as National Cybersecurity Awareness Month (NCSAM), a campaign aimed at raising awareness about the significance of cybersecurity and promoting safe practices online.

The Dangers of Using Unknown USB Drives: What You Need to Know USB devices have become ubiquitous. They are used for everything from transferring data

iPhones are known for their reliability and user-friendly interface; however, like any technology, they can experience issues from time to time. Here’s a list of

Wi-Fi hiccups refer to intermittent connectivity issues that can disrupt the normal functioning of a wireless network. These disruptions manifest as brief drops in connection,

Here are some practical tips for addressing common IT issues that users may encounter, along with straightforward solutions. 1. Slow Computer Performance Close Unnecessary Applications: Limit
A keylogger is a type of surveillance software or hardware designed to record keystrokes made by a user on their keyboard. This technology can be

Cybercrime is a growing concern that affects individuals, businesses, and organizations worldwide. As technology evolves, so do the methods that cybercriminals use to exploit unsuspecting

Reliable IT support is essential for businesses of all sizes. Whether you’re a small business owner or part of a larger corporation, the right IT

Businesses face a multitude of risks that can disrupt operations and lead to significant financial losses. Natural disasters, equipment failures, cyberattacks, and human errors can

Backup internet, also known as a secondary or redundant internet connection, refers to an additional internet service that is set up to provide a failover

Microsoft Outlook is a powerful email and calendar application, but many users only scratch the surface of its capabilities. Here are 10 features of Outlook

Securing your home against intruders involves a combination of physical security measures, technology, and good practices. Here are comprehensive steps you can take to enhance

Here are the top tips and tricks for Microsoft Word that can help both beginners and experienced users enhance their productivity: 1. Utilize Keyboard Shortcuts Mastering
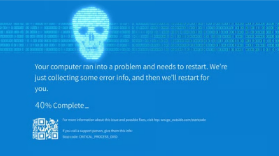
The “Blue Screen of Death” (BSOD), officially known as a Stop Error, is a critical error screen displayed by the Microsoft Windows operating system when

Reacting with emojis in Outlook can add a fun and expressive touch to your emails, but it works a bit differently depending on whether you

Here are five tips to enhance your experience and usability on Facebook: 1. Privacy Settings Management Regularly review and adjust your privacy settings to control who

Choosing the right wall mount for your TV is essential to enhance your viewing experience while ensuring safety and aesthetics. Here’s a detailed guide to

Preventing common iPhone issues can help extend the life of your device and ensure that it runs smoothly. Here are some practical tips to help

Bandwidth throttling is when your Internet Service Provider (ISP) intentionally slows down your internet speed based on your usage patterns. To help mitigate or avoid

Upgrading your computer can enhance its performance and extend its lifespan. Here are some signs that indicate it might be time for an upgrade: 1. Slow

Determining whether you need a Virtual Private Network (VPN) depends on your online activities and concerns about privacy and security. Here are some signs and

IoT (Internet of Things) devices refer to a wide range of physical objects that are connected to the internet, allowing them to collect, send, and

Overloading your router with too many devices can lead to slower speeds, connectivity issues, and overall reduced network performance. Here are several signs and methods

Several factors and physical obstacles can interfere with the signal of a Wi-Fi router, causing reduced performance and connectivity issues. Here are some common obstructions:

Here are five compelling reasons for needing security cameras: Enhanced Security and Crime Deterrence: Security cameras act as a strong deterrent against criminal activity, such

Proficiency in Microsoft Office programs like Word, Excel, and PowerPoint is crucial for creating various types of documents and presentations. Here’s a brief overview of

Understanding email etiquette is important for effective communication in both personal and professional settings. Here are some key guidelines to follow: Use a Professional Email

Using search engines effectively can significantly enhance your ability to find accurate and relevant information. Here are some tips to help you get better results:

Understanding how to identify and solve common computer problems involves several key steps: Identifying Software Issues: Symptoms: Recognize signs such as slow performance, crashes, or

Fake Prize or Cash Reward Never enter Venmo log-in information outside of Venmo.com and the Venmo app. Venmo will only email you from an address

Familiarize Yourself with the Desktop Layout: Take a moment to understand the layout of your desktop, including the taskbar (or dock), the desktop icons, and

An operating system (OS) is fundamental software that acts as an intermediary between computer hardware and the user. It provides a user interface, manages hardware

Identifying a scam can be challenging, but there are several key signs and strategies you can use to help distinguish between a scam and a

Here are some troubleshooting steps you can try to fix the speaker issue on your iPhone: Check Volume: Ensure that the volume is turned up.

A blue screen on your computer, commonly known as the “Blue Screen of Death” (BSOD), usually indicates that the operating system has encountered a critical

Creating a rule in Microsoft Outlook Mail can help you manage your incoming emails more efficiently. Here are the steps to create a rule in

If you’ve cleared your browsing history and now your passwords aren’t being saved in your browser, it could be due to a few different reasons.

While it’s challenging to provide absolute certainty that any device, including an iPhone, has never been hacked, there are several steps you can take to

Cloud storage services refer to an online storage solution that enables users to save, manage, and access data over the internet instead of relying solely

Transferring data from one computer to another can be accomplished through several methods, depending on the amount of data, the types of computers involved, and

A Managed Service Provider (MSP) can play a crucial role in protecting your office from a data breach by implementing various security measures, providing ongoing

If your Wi-Fi connection keeps turning off, it can be frustrating and disruptive. Here are several common reasons why this issue might occur, along with

Here are the top 20 tips to help save time and improve efficiency in your business operations: 1. Automate Repetitive Tasks Use software tools to automate

Data entry errors can lead to significant issues in business operations, including financial discrepancies and poor decision-making. Here are five ways to reduce or avoid

To protect yourself from personalized spear-phishing attacks, it’s important to recognize specific red flags that may indicate an attempt to deceive you. Here’s a list

If you’re unable to see your internet network from the list of available networks on your device, there could be several reasons for this issue.

AI tools can significantly enhance operations, improve customer service, and drive growth in various ways across different industries. Here’s how: 1. Enhancing Operations Automation of

Streaming to YouTube can be relatively easy, especially with the right tools and preparation. Here are the basic steps to get started with live streaming

If you’ve forgotten your password on your Samsung tablet, there are several methods you can use to reset it. Here are some options: Option 1:

If your iPhone photos are no longer syncing to your iMac, there could be several reasons for this issue. Here are some common causes and

The Sweep feature in Outlook Mail is a convenient tool designed to help users manage and organize their email inboxes more efficiently. It allows you

Yes, data can often still be retrieved from a dead computer, depending on the nature of the failure. Here are some common methods: Hard Drive
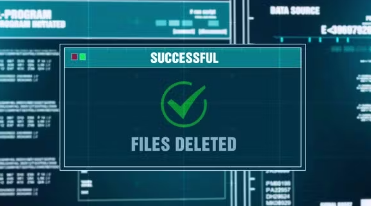
If you’ve accidentally deleted files or data, there are several methods you can try to recover them: Check Recycle Bin (Windows) or Trash (Mac): The

Implementing proper data backup and recovery practices is crucial to protect your important files and ensure you can recover them in case of data loss.

To customize settings on your device, you typically need to access the Settings app or menu. Here’s how you can find and customize settings on

Customizing settings on your device can enhance usability and tailor the user experience to your preferences. Here are steps to customize settings on your device

To resolve common email problems and errors, you can follow these general troubleshooting steps: Check Internet Connection: Ensure you have a stable internet connection before

Common signs of a malware infection on your device include: Slow Performance: If your device suddenly becomes slow, unresponsive, or sluggish, it could be a

To improve your device’s performance, here are some steps you can take: Update Software: Ensure your device’s operating system, drivers, and software applications are up

If your device is not connecting to the internet, here are some troubleshooting steps you can follow: Check the Basics: Make sure your device’s Wi-Fi

If your iPhone is opening apps on its own, it could be due to a few different reasons: Software Glitch: Sometimes, software glitches or bugs

A security system typically includes a combination of various components such as cameras, sensors, alarms, and monitoring services to help protect your home or business

You can send a fax from a computer using an online fax service or by using a fax modem connected to your computer. Here’s how

The TP-Link Deco Pro is considered a good router system for home or small office use, offering reliable Wi-Fi coverage and performance. Some key features

Some of the new features in Windows 11 include: Redesigned Start Menu and Taskbar: The Start Menu is now centered, and the Taskbar icons have

Keyboard shortcuts can be quite helpful for improving productivity. Here are some essential keyboard shortcuts for you: Ctrl + C / Cmd + C – Copy

Here are some time management tips that you may find helpful: Set specific goals: Define what you want to accomplish and break them down into

Organizing your Outlook inbox can help you manage your emails more efficiently and stay on top of important messages. Here are some tips to help

Ensure proper ventilation for your electronic devices by keeping them in well-ventilated areas. Avoid direct sunlight exposure on your electronics as heat buildup can cause

Excel functions and data validation are powerful tools that can streamline data analysis, improve accuracy, and enhance productivity. Here are some examples of how they

Some signs that an email may be a scam include: Unknown sender: If you receive an email from an unknown sender or a suspicious email

Cell phones can be vulnerable to hacking through various methods. Here are some common ways your cell phone could be hacked: Malicious Apps: Downloading apps

If you have forgotten your LastPass master password and need to access your stored passwords, you can attempt account recovery through LastPass. Here are some

Here are the top 3 IT tips to help you stay secure and efficient: Regularly Backup Your Data: It’s crucial to regularly back up your

Outlook offers several features that can enhance productivity and organization. Some of the best features to use in Outlook mail include: Focused Inbox: This feature

Network cabling refers to the physical cables used to connect various network devices together to enable communication and data transfer. These cables are essential for

Whether you need a VPN depends on your specific circumstances and online activities. A VPN can provide benefits like enhanced security and privacy by encrypting

Access to high-speed internet is crucial for both personal and professional tasks. Two prominent technologies that have revolutionized internet connectivity are Fiber 1G and 5G

You can easily create and use email templates in Outlook for efficient communication. To create an email template in Outlook, you can follow these steps:

There are several steps you can take to potentially speed up your PC: Uninstall unnecessary programs and apps. Disable startup programs that you don’t need.

Using rice to dry up water on a phone is a common household remedy that has been popular for years. The idea behind using rice

If you’ve accidentally spilled coffee on your computer, it’s important to act quickly to minimize damage. Here are some steps you can take after a

Business IT services offer a wide range of specialized solutions and support tailored to meet the technology needs of organizations. Here are some key benefits

PC and Mac are two different types of computers with distinct characteristics and differences. Here are some key contrasts between a PC (Personal Computer) and

Keeping your iPhone protected is essential to safeguard your personal information and ensure the security of your device. Here are some basic steps you can

Using Excel pivot tables provides various benefits, including: Data Summarization: Pivot tables allow users to summarize large amounts of data into a concise, understandable format,

Excel stands out as a versatile tool that offers a wide range of features to create insightful reports. From basic tables to advanced visualizations, Excel

Getting a popup message asking you to call Microsoft can sometimes be a sign of a tech support scam. Scammers often use pop-up messages claiming

MFA, or multi-factor authentication, is an added layer of security where users are required to provide two or more forms of verification before gaining access

Antivirus software plays a crucial role in keeping a business safe from various cyber threats and malware. Here are some ways antivirus software helps protect

Minimizing human errors in business is crucial for enhancing productivity, efficiency, and overall performance. Here are some strategies to help reduce human errors in the

Set up Rules and Filters: Use Outlook rules to automatically sort and categorize incoming emails. You can create rules based on sender, subject, keywords, or

Cleaning up your iCloud account can help you optimize storage space and organize your data more efficiently. Here are some steps to clean up your

Whether your website serves as an effective marketing tool depends on various factors. Here are some considerations to help you evaluate if your website is

Pros: Cost-Effective: VoIP services are often cheaper than traditional phone services, especially for long-distance or international calls. Scalability: VoIP systems are easily scalable, making it

Here are 5 tips to keep in mind when using PowerPoint for your presentations: Less Text, More Visuals: Use visuals such as images, graphs, and

Where concerns about safety and security are at the forefront of many homeowners’ minds, investing in a home security system has become increasingly important. A

AI technology has a wide range of applications across various fields and industries. Here are some common uses of AI: Virtual Assistants: AI-powered virtual assistants

There are several common signs that can indicate you are being scammed. Here are some of the most obvious ones to watch out for: Unsolicited

A 404 error is an HTTP status code that indicates the server could not find the requested webpage. This error occurs when a user tries

Managed services can be incredibly beneficial for businesses and organizations for several reasons: Cost-Effective: Managed services typically work on a subscription-based model, allowing businesses to

Here are some tips to save electricity when using your PC: Adjust Power Settings: Set your PC to sleep or hibernate after a period of

Working smarter in Outlook can help boost productivity and efficiency. Here are some tips to help you make the most of Outlook: Keyboard Shortcuts: Learn

There are several warning signs that may indicate your computer is nearing the end of its life cycle. Here are some common indicators to watch

Ensuring the security of your smartphone is crucial in this digital age. Here are some tips to help keep your smartphone secure: Set a Strong

Streaming on YouTube can be a great way to connect with your audience. Here are some tips to improve your streaming experience: Plan Your Content:

Here is a basic checklist that you can follow: Strong and Unique Passwords: Use unique passwords for each account and make sure they are strong

There are several ways to speed up a Windows PC: Disable startup programs: Open the Task Manager (Ctrl + Shift + Esc), go to the

Understanding computers is essential in today’s digital age. Here are five key things everyone should know about computers: Hardware vs. Software: Computers consist of hardware

Home security surveillance is critical for safeguarding your property and giving you peace of mind. By implementing the right practices and avoiding common pitfalls, you

Building your online presence is crucial for branding. Here are some tips to help you establish a strong online presence: Define your brand: Clearly define

Prioritize tasks: Identify the most important tasks and focus on completing them first. Set specific goals: Break down your goals into smaller, manageable tasks and

As unpredictable weather events become more frequent and severe, businesses must prioritize preparedness and resilience to minimize disruptions, protect assets, and ensure the safety of

Marketing is essential for attracting customers, driving sales, and building brand awareness for your business. Here are the top five effective ways to market your

Protecting your office from a data breach is essential to safeguard sensitive information, maintain client trust, and comply with data protection regulations. Here are some

Investing in Information Technology (IT) is essential for the growth and success of modern businesses, but it comes with its share of challenges and potential

Technology and Artificial Intelligence (AI) are poised to revolutionize the future in profound ways, impacting various aspects of our lives, society, and industries. Here are

Life is a continuous journey of learning, growth, and adaptation, and navigating its complexities requires creativity, resourcefulness, and strategic thinking. Similarly, in the fast-paced world

Your home is your sanctuary, a place of comfort, safety, and belonging. Protecting your home and loved ones from potential threats is paramount in maintaining

Networking is more than just a buzzword – it’s a powerful tool that plays a crucial role in professional success, personal growth, and building valuable

Staying productive and organized while on the go is crucial for maximizing efficiency and managing daily tasks effectively. Fortunately, there is a wide range of

Our reliance on computers for work, communication, entertainment, and more has never been greater. However, like any electronic device, computers can encounter issues that may

LOL – Laugh Out Loud BRB – Be Right Back OMG – Oh My God IDK – I Don’t Know TTYL – Talk To You

Integrating interactive content into your website can be a powerful way to engage visitors, encourage them to spend more time on your site, and increase

Speeding up a Windows PC can significantly enhance your overall computing experience. Here are some effective tips to optimize the performance of your Windows computer:

Cybersecurity has become more important than ever. With the burgeoning number of cyber threats looming online, having robust protection for your devices is non-negotiable. This

In the vast realm of the internet, two terms that often pop up are ‘cookies’ and ‘cache’. While they may sound like fancy technical jargon,

Keyboard shortcuts are incredibly useful for saving time and boosting productivity while working on a computer. Here are some of the best keyboard shortcuts across
Setting up a signature in Outlook is a great way to add a professional touch to your emails. A signature typically includes your name, company

Encryption is a method of encoding information in such a way that only authorized parties can access and understand the data. It involves converting plaintext

Imagine a bustling digital metropolis where websites are the storefronts, each uniquely designed to showcase products, services, and information to visitors from around the world.

Excel is a versatile and powerful tool for data analysis, calculation, and organization, widely used by professionals in various industries. Whether you’re a beginner or

Azure is Microsoft’s cloud computing platform that offers a wide range of services and resources to support businesses, developers, and IT professionals in building, deploying,

Reducing printing costs is a practical way for individuals and businesses to save money, minimize waste, and promote sustainability. By adopting efficient printing practices and

iPhone repairs are a common necessity for many iPhone users, whether due to accidental damage, hardware issues, or general wear and tear. When faced with

TV mount installations are a popular choice for homeowners and businesses looking to enhance their viewing experience, optimize space, and achieve a sleek, modern look

Windows 11, Microsoft’s latest operating system, introduces a range of new features and enhancements designed to improve productivity, creativity, and overall user experience. From a

When faced with an internet outage or unavailability, it can be frustrating and disruptive, especially in today’s connected world where we rely heavily on internet

Experiencing a Microsoft popup scam on your computer can be quite unsettling, but it’s important not to panic and to address the issue calmly and

Using email safely is essential in today’s digital age to protect sensitive information, maintain privacy, and prevent cyber threats. With the increasing prevalence of email

Enhancing your online business presence is essential in today’s digital landscape to attract customers, build brand credibility, and drive growth. By implementing effective strategies and

Clearing the browser cache in popular web browsers like Chrome, Firefox, and Edge is a crucial maintenance task to improve performance, free up storage space,

What is a VoIP Phone System? A VoIP phone system, also known as internet telephony or IP telephony, converts analog voice signals into digital data

When it comes to selecting a reliable Wi-Fi router for your home, there are several factors to consider such as speed, range, ease of set-up,

To search like a pro and get the most relevant results when using Google or any other search engine, consider the following tips: Use Specific

Whether to power off your computer or leave it on depends on your usage patterns and personal preferences. Here are some factors to consider when

To password protect a Word document and keep its contents secure, follow these steps using Microsoft Word: Open Your Word Document: Start by opening the

Typing special symbols can be done in various ways depending on the operating system and device you are using. Here are some common methods to

A company’s computer network is the backbone of its operations. From communication and collaboration to data storage and security, a reliable and well-maintained network is

Boosting your new laptop’s performance can be a great way to maximize its capabilities. Here are five steps to help you get started: Uninstall Unnecessary

Our computers are essential tools for work, communication, entertainment, and more. With so much reliance on these devices, it’s important to keep them clean and

VoIP, which stands for Voice over Internet Protocol, is a technology that allows you to make voice calls using a broadband internet connection instead of

To prevent accessing malicious or harmful websites, here are some tips: Use Antivirus Software: Install reputable antivirus software on your device to help block known

A Managed Service Provider (MSP) offers various IT services to help manage and support your organization’s IT infrastructure and systems. Some common services provided by

Being scammed on your computer can be a challenging and alarming experience. Whether it’s a fake tech support call, a phishing email, or a fraudulent

When it comes to choosing a laptop, two prominent names that often come to mind are Dell and HP. Both companies offer a wide range

In today’s digital age, ensuring the safety and security of your home has never been more important. With advancements in technology, home security systems have

Stable Internet Connection: A stable and high-speed internet connection is crucial for smooth streaming of live TV. Make sure your internet speed meets the requirements

Grammarly is an AI-powered writing assistant that goes beyond traditional spellcheckers and grammar tools to provide comprehensive writing support across various genres and styles. From

In the age of ubiquitous connectivity, your router plays a crucial role in ensuring seamless internet access and optimal performance for all your devices. However,

In today’s hyper-connected world, where cyber threats lurk around every virtual corner, the need for internet security training has never been more critical. As cyberattacks

In today’s digital age, where information is the new currency, the cloud has emerged as a game-changer, offering unparalleled convenience and accessibility. However, as organizations

Disposing of old electronics, also known as e-waste, requires special care to prevent environmental pollution and protect your personal data. Here are some guidelines on

Protecting your identity online is important to safeguard your personal information from potential threats. Here are some tips to help you protect your identity on

Unsubscribing from legitimate marketing emails sent by reputable companies can be an effective way to reduce the amount of unwanted emails you receive. When you

Reports have surfaced of a new breed of cyber scam involving Microsoft. Scammers are targeting unsuspecting individuals with fake messages claiming that their systems are

Firewalls come in several types, each offering unique features and functionalities tailored to diverse cybersecurity needs. Understanding the different types of firewalls can help organizations

Firewalls stand as an integral component of cybersecurity infrastructure, playing a pivotal role in protecting devices, networks, and sensitive data from a wide array of

Firewalls form the cornerstone of cybersecurity, serving as a vital barrier between your devices and the dangers lurking on the internet. In its simplest form,

Spam and phishing schemes have become pervasive in today’s digital landscape, with cybercriminals employing increasingly sophisticated tactics to trick individuals into divulging sensitive information or

When it comes to choosing a laptop, the brand you opt for can significantly impact your overall computing experience. With a multitude of laptop brands

LastPass is a renowned password management tool designed to simplify and secure the way you store and manage your passwords. In today’s digital age, where

In the fast-paced digital landscape of today, the ability to analyze large volumes of data efficiently and effectively can provide invaluable insights and drive strategic

Microsoft Word is a versatile word processing tool that offers a wide array of features to help users create, edit, format, and collaborate on documents

A managed service provider (MSP) is a third-party company that offers a range of IT services to businesses, organizations, or individuals. MSPs are responsible for

In today’s digital age, personal computers are essential tools for work, entertainment, and connectivity. However, the energy consumption associated with operating a PC can contribute

In a world where email communication is ubiquitous, managing your inbox efficiently can be a challenge. Sorting through a deluge of emails to find the

In today’s digital age, cybersecurity threats pose a significant risk to businesses of all sizes. One crucial tool in the fight against these threats is

There are several useful Chrome extensions that can help increase productivity. Here are a few popular ones: Grammarly: A writing assistant that helps you with

In the dynamic and competitive landscape of modern business, organizations are constantly seeking ways to optimize their IT infrastructure, enhance operational efficiency, and drive innovation.

In the rapidly evolving world of technology, staying abreast of the latest trends and buzzwords is essential for small and medium-sized businesses (SMBs) looking to

In the fast-paced digital landscape of today, where attention spans are fleeting and search engine algorithms constantly evolve, maintaining a dynamic and engaging online presence

In today’s digital age, remote work, flexible schedules, and the need for secure and scalable IT solutions have become more prevalent than ever. One technology

Here are some critical security flaws that SMBs should prioritize fixing to enhance their cybersecurity posture: Weak Passwords: Encourage employees to use strong, unique passwords

In the age of remote work, effective leadership plays a crucial role in ensuring the success, productivity, and well-being of remote teams. As a manager

Here are some browser tips to enhance your browsing experience: Use Keyboard Shortcuts: Learn common keyboard shortcuts for faster navigation. For example, Ctrl + T

Keep Your PC Clean: Regularly clean the exterior of your PC to prevent dust buildup. Dust can clog vents and fans, leading to overheating. Use

In today’s digital-driven world, an effective online marketing strategy is crucial for attracting, engaging, and converting visitors on your website. To maximize the impact of

In today’s digital age, social media has transformed the way businesses connect with their customers, promote their brand, and drive growth. With billions of active

In today’s digital world, preserving and protecting your valuable data is paramount. Having reliable computer backups in place is essential to safeguard against data loss,

In the digital age, personalized advertising has become ubiquitous on the internet, with ads tailored to our interests, behaviors, and online activities. Have you ever

In the vast and interconnected world of the internet, every device connected to the network is identified by a unique numerical label known as an

A stable and reliable internet connection is essential for seamless online activities, whether for work, entertainment, or communication. However, internet connection issues can occur unexpectedly,

In today’s digital age, encountering computer issues is almost inevitable. From slow performance to sudden crashes, computer problems can disrupt your workflow and cause frustration.

Solid-state drives (SSDs) and hard disk drives (HDDs) are two types of storage devices commonly used in computers and laptops. While both serve the primary

Setting up a Virtual Private Network (VPN) is a proactive measure to enhance your online security and privacy by encrypting your internet connection and masking

In today’s digital landscape, where cyber threats are constantly evolving and becoming more sophisticated, having robust cybersecurity measures in place is paramount. One company that

If you’re experiencing a slow computer or laptop, there are several steps you can take to improve its performance and speed up its operation. Here

Improving your Wi-Fi signal strength at home is essential for a seamless and reliable internet experience. Weak Wi-Fi signals can lead to slow speeds, dropped

Dealing with a computer virus or malware infection can be a stressful experience, but taking immediate action is essential to minimize damage and protect your

Losing important files or accidentally deleting them from your device can be a nightmare, especially when those files contain valuable information, memories, or work-related data.

Security cameras have become indispensable tools for monitoring and safeguarding homes, businesses, and public spaces. Whether you’re considering installing a new security camera system or

Voice over Internet Protocol (VoIP) has revolutionized communication by enabling voice calls over the Internet, offering an alternative to traditional landline services. While VoIP presents

In today’s interconnected world, the need for reliable internet access is more crucial than ever. Internet hotspots have become indispensable for staying connected while on

As smartphones have become an integral part of our lives, ensuring the security of our iPhones is paramount. iPhones, known for their robust security features,

The strategic allocation of resources toward information technology (IT) has become a fundamental imperative for organizations across industries. Budgeting for IT expenses serves as a
The importance of IT risk assessment cannot be overstated. From data breaches and cyber attacks to system failures and compliance lapses, the realm of information

There are several signs to look out for in order to avoid falling victim to scams. Here are some common signs to beware of: Unsolicited

In the realm of modern financial convenience, Venmo stands as a trailblazer, streamlining the process of sending and receiving money through a user-friendly mobile platform.

Microsoft Excel is a powerful tool for data organization, analysis, and visualization, with capabilities that extend far beyond simple number crunching. In this blog, we

Attracting more visitors to your website is crucial for expanding your online presence, engaging with potential customers, and ultimately driving business growth. This blog serves
In an increasingly digital world, where businesses rely on interconnected systems and data flows, network security has never been more critical. The threat landscape continues

Use Focused Inbox: Outlook’s Focused Inbox automatically sorts your inbox into two tabs—”Focused” and “Other.” It intelligently prioritizes important emails in the Focused tab, helping

In today’s digital age, where virtually every aspect of our lives has become intertwined with the internet, the importance of robust password management cannot be

In the digital age, where individuals interact with a multitude of applications and systems throughout their day, managing numerous login credentials can be cumbersome and

In the rapidly evolving landscape of digital operations, the criticality of safeguarding data, applications, and systems from potential losses or disruptions is paramount. The concepts

Microsoft Teams has emerged as a leading platform for communication, collaboration, and productivity in the modern workplace. With its comprehensive range of features, Teams enables

Robocalls have become an increasingly prevalent nuisance, with automated systems inundating phone lines with unsolicited calls ranging from spam marketing to fraudulent schemes. These calls

Navigating your Windows operating system doesn’t have to be a laborious, point-and-click affair. Keyboard shortcuts offer a faster, more efficient way to perform common tasks,

In today’s interconnected digital landscape, communication has evolved beyond traditional boundaries, allowing people to connect and interact seamlessly across distances. At the forefront of this

In the fast-paced and ever-evolving landscape of information technology, a skilled and well-rounded IT team is essential for an organization’s success. However, identifying and addressing

In an age where digital communication is ubiquitous, email scams have become increasingly prevalent, targeting individuals and organizations with deceptive schemes. Recognizing the signs of

In today’s interconnected digital landscape, networks and applications serve as the backbone of modern business operations. However, as technology evolves at a rapid pace, older
Technology has become an indispensable tool for businesses seeking to achieve growth and success in today’s digital age. From streamlining operations to enhancing customer experiences,

In today’s rapidly evolving business landscape, organizations are faced with the increasing complexity of managing their IT infrastructure and technology needs. From network and security

In today’s digital age, streaming media has transformed the way we consume entertainment. Gone are the days of cable subscriptions and limited content options. With

The Internet of Things (IoT) has become a buzzword in recent years, promising to revolutionize the way we live and interact with our surroundings. From

In today’s digital age, computers have become an integral part of our lives. However, like any complex technology, they can sometimes encounter issues that hinder

As smartphones have become an integral part of our lives, ensuring the security of our iPhones is paramount. iPhones, known for their robust security features,

With the rise of advancements in technology, remote working has become an increasingly popular option for individuals and companies alike. Remote work offers flexibility, efficiency,

In today’s digitally connected world, internet speeds play a crucial role in our online experiences. Whether you are streaming your favorite TV show, attending virtual
Managed IT services refer to the practice of outsourcing the responsibility for managing, monitoring, and supporting an organization’s IT systems and infrastructure to a third-party

In today’s technology-driven landscape, the threat of cyberattacks looms large, impacting individuals and businesses alike. Being hacked can have severe consequences, leaving victims vulnerable to

In recent years, cloud computing has revolutionized the way businesses and individuals store, access, and manage their data and applications. The cloud offers numerous benefits,

Security systems are designed to protect homes and properties by preventing unauthorized access, detecting potential threats, and alerting homeowners or authorities when necessary. Here are

Phishing is a type of cyber attack where hackers attempt to deceive individuals into revealing sensitive information such as passwords, credit card details, or social

Malware refers to malicious software designed to cause harm to computer systems or steal sensitive information. It can include viruses, worms, trojans, ransomware, spyware, adware,

Welcome to our website! In today’s digital era, websites play a crucial role in establishing an online presence for businesses and individuals alike. One valuable

The way we communicate has evolved significantly over the years. From relying on traditional landline telephones to embracing cutting-edge technologies, the shift towards digital communication
If you own or manage a business then cybersecurity should be at the forefront of your mind. The amount of cyber threats and attacks are
Did you know that unified communications is an incredibly important business concept? In fact, a unified communications strategy will provide your organization with the ability

The modern office space that runs on technology should and can be a thing of absolute beauty. Long gone are the days when endless rows

The fact that a great deal of organizations have shifted some or all in-house information technology operations to a managed IT service provider is not